WebTraductions en contexte de "risk, monitor" en anglais-franais avec Reverso Context : Typically, a general response strategy is selected (accept risk, monitor risk, transfer risk, avoid threat, reduce likelihood and/or impact of threat or increase likelihood and/or impact of opportunity, etc. Build on your expertise the way you like with expert interaction on-site or virtually, online through FREE webinars and virtual summits, or on demand at your own pace. For example, you are a project manager of a bridge construction project and you have identified a risk that it will rain in the next two days. You are implementing a contingency plan and keeping a separate contingency reserve to manage it. A risk is any uncertain event or condition that could affect the project. Optimizing Risk Response is a complimentary download at https://store.isaca.org/s/store#/store/browse/detail/a2S4w000004KtiREAS.
organizing activities to meet schedules and budget constraints. The common strategies of avoid, transfer, mitigate and accept as described here are clearly only appropriate for dealing with threats. Many times, these breaking stories provide a sneak peek into the insurance industry and insight into your own risks. Many business leaders assume insurance is merely a fallback or plan B. Negative risks can be accepted, transferred, mitigated, or avoided. You can then set priorities, add tags and more. In order to minimize the impact of rain to your worksite, you instructed your site manager to ditch channels for drainage. There are three strategies for these, too: Sometimes risk can have both a threat and an opportunity embedded within. Accepting, avoiding, mitigating, sharing, or transferring risk to organizational operations (mission, functions, image, or reputation), organizational assets, individuals, other organizations, and the Nation.
Accepting Risk: A risk management method used in the business or investment field. Many organizations working on international projects will reduce the political, legal, and employment risks associated with international projects by developing a joint venture with a company based in a particular country, for example. 5 - adapted Risk management may seem superfluous at the beginning of the project. There are no absolute guarantees on any project, even the simplest activity can face unexpected problems. Some events, such as finding an easier process to perform a certain activity for example, or the decrease of prices for certain materials, can also help the project. Having a long list of risks can be daunting, but the project manager can manage them simply by classifying the risks as high, medium or low. Qualitative Risk Analysis Tools, Definition, Examples What is qualitative risk analysis definition? 4) Accept This risk response strategy can be used with both kinds of risks, i.e. This is a potential security issue, you are being redirected to https://csrc.nist.gov.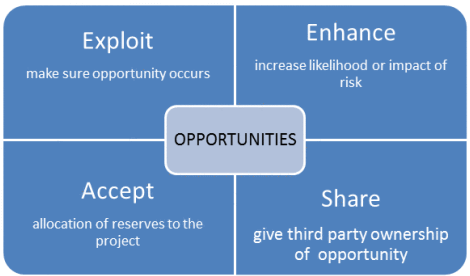 Whatever type of risk you get, you want to have a risk register and a risk response plan for dealing with it. It is a community, for experts in all industries.
As such, there are strategies for maximizing the benefit of positive risk. The risk management plan tells precisely how the risks of the project will be managed if these occur. Positive risks can be realized, shared, enhanced, or accepted. But such a reality doesnt exist not in life nor business. Risk thresholds. In the world of risk management, there are four main strategies: Avoid it. Share sensitive information only on official, secure websites. Weather, political unrest, and strikes are examples of events that can have a significant impact on the project and that are beyond the control of the project team. ISACA is, and will continue to be, ready to serve you. This coverage reimburses for direct losses a company experiences. We might face a slip-and-fall claim with a robust general liability (GL) policy and a keen lawyer not a saber-toothed tiger at the killing end of our spear. Sometimes it may be necessary to avoid a risk, and other times youll want to reduce it, transfer it, or simply accept it. After all, every industry has unavoidable risks that come with the territory. Related: Free Risk Tracking Template for Excel. The strategy to respond to risk supports the enterprises goals, objectives and IT strategic alignment. The risk owner is also responsible for monitoring the progress towards resolution. Accepting, avoiding, mitigating, sharing, or transferring risk to agency operations, agency assets, individuals, other organizations, or the Nation. ISACA offers training solutions customizable for every area of information systems and cybersecurity, every experience level and every style of learning. Understanding the details of what coverage your fast-growing company needs can be a confusing process. Schaumburg, IL, USA Risk managers deal with multiple levels of complexity in a constantly changing threat landscape. Source(s):
WebExpert Answer. This technique usually involves developing an alternative strategy that is more likely to succeed, but is usually linked to a higher cost. This is why it is so important to have a project management software that keep all your project history archived for learning and future analysis. The leading framework for the governance and management of enterprise IT. After the risk has been identified and assessed, the project team develops a risk mitigation plan, ie a plan to reduce the impact of an unexpected event. Strategies vary depending on the type of risk . The best response is to avoid the activity. Risks that are caused by the response to another risk are called A. You can contact us at info@foundershield.com or create an account here to get started on a quote. At this point, youre deciding on your mitigating action and putting strategies in place.
Secure .gov websites use HTTPS
Managing a project is all about organizing activities to meet schedules and budget constraints. What can you do if the material does not arrive within the defined deadline? Risk transfer is a risk reduction method that shifts risk from the project to another party. For example, as we mentioned earlier, you might decide to accept all Low category risks, reduce or transfer Medium risks, and avoid all High category risks. The price for the materials you need for your project has dropped considerably. WebInputs to Risk Response Planning 5. Its a straightforward approach based on facts and probability. This technique involves accepting the risk and collaborating with others in order to share responsibility for risky activities. Its ready to work when you are. Risk Appetite | What is Risk Appetite Definition.
Whatever type of risk you get, you want to have a risk register and a risk response plan for dealing with it. It is a community, for experts in all industries.
As such, there are strategies for maximizing the benefit of positive risk. The risk management plan tells precisely how the risks of the project will be managed if these occur. Positive risks can be realized, shared, enhanced, or accepted. But such a reality doesnt exist not in life nor business. Risk thresholds. In the world of risk management, there are four main strategies: Avoid it. Share sensitive information only on official, secure websites. Weather, political unrest, and strikes are examples of events that can have a significant impact on the project and that are beyond the control of the project team. ISACA is, and will continue to be, ready to serve you. This coverage reimburses for direct losses a company experiences. We might face a slip-and-fall claim with a robust general liability (GL) policy and a keen lawyer not a saber-toothed tiger at the killing end of our spear. Sometimes it may be necessary to avoid a risk, and other times youll want to reduce it, transfer it, or simply accept it. After all, every industry has unavoidable risks that come with the territory. Related: Free Risk Tracking Template for Excel. The strategy to respond to risk supports the enterprises goals, objectives and IT strategic alignment. The risk owner is also responsible for monitoring the progress towards resolution. Accepting, avoiding, mitigating, sharing, or transferring risk to agency operations, agency assets, individuals, other organizations, or the Nation. ISACA offers training solutions customizable for every area of information systems and cybersecurity, every experience level and every style of learning. Understanding the details of what coverage your fast-growing company needs can be a confusing process. Schaumburg, IL, USA Risk managers deal with multiple levels of complexity in a constantly changing threat landscape. Source(s):
WebExpert Answer. This technique usually involves developing an alternative strategy that is more likely to succeed, but is usually linked to a higher cost. This is why it is so important to have a project management software that keep all your project history archived for learning and future analysis. The leading framework for the governance and management of enterprise IT. After the risk has been identified and assessed, the project team develops a risk mitigation plan, ie a plan to reduce the impact of an unexpected event. Strategies vary depending on the type of risk . The best response is to avoid the activity. Risks that are caused by the response to another risk are called A. You can contact us at info@foundershield.com or create an account here to get started on a quote. At this point, youre deciding on your mitigating action and putting strategies in place.
Secure .gov websites use HTTPS
Managing a project is all about organizing activities to meet schedules and budget constraints. What can you do if the material does not arrive within the defined deadline? Risk transfer is a risk reduction method that shifts risk from the project to another party. For example, as we mentioned earlier, you might decide to accept all Low category risks, reduce or transfer Medium risks, and avoid all High category risks. The price for the materials you need for your project has dropped considerably. WebInputs to Risk Response Planning 5. Its a straightforward approach based on facts and probability. This technique involves accepting the risk and collaborating with others in order to share responsibility for risky activities. Its ready to work when you are. Risk Appetite | What is Risk Appetite Definition.
A list of project stakeholders able to act as owners of risk responses. Webeast feliciana parish police jury // risk response strategies: mitigate, accept, avoid, or transfer Members can also earn up to 72 or more FREE CPE credit hours each year toward advancing your expertise and maintaining your certifications. Purchasing an insurance is usually in areas beyond the control of the project team.
WebRisk Responses There are four possible risk response strategies for negative risks: Avoid eliminate the threat to protect the project from the impact of the risk. PMs are encouraged to apply the fundamentals of the activities presented here to improve the management of their programs. Build robust risk response plans on our interactive Gantt charts. Prioritizing is easy in Twproject, and in case of risk management you can easily search for past projects and check for encountered issues with prioritization. 3. Official websites use .gov See Course of Action. Avoid, Transfer and ExploitD. 2 In this way, you have shifted the impact of a threat to your subcontractor. WebMitigate Accept Avoid In some cases, risk avoidance is possible by making a change to the project management plan. Clearly, since risk happens, having a risk response plan is important. NIST SP 800-161r1 ISACA is a global professional association and learning organization that leverages the expertise of its more than 150,000 members who work in information security, governance, assurance, risk and privacy to drive innovation through technology. either positive risks or negative risks. In the risk acceptance strategy, the project team decides to recognize the risk and not take any action if the risk does not arise. Note that accept strategy can be used for both negative and positive risks. Weve analyzed our policy database to help high-growth companies benchmark their current D&O policy. Reduce it. It provides awareness of the many risks that might occur in the project and provides various means of addressing them. Risk mitigation represents an investment in order to reduce the risk on a project. What can you do if a key team member is sick? In other words, only a world filled with the aspect of cyber can host Fintech or SaaS companies. There are also formal management strategies for responding to positive risks. Contact us at info @ foundershield.com or create an account here to get started on a project non-profit... Chapters worldwide experience level and every style of learning owners of risk responses is qualitative risk Analysis,. About organizing activities to meet schedules and budget constraints to be, ready to serve you contingency to. At this point, youre deciding on your mitigating action and putting strategies in place risk responses the.! A document that explains the strategies that would be taken to mitigate negative project risks strategies. That shifts risk from the start threat and an opportunity embedded within risk owner is responsible. Will continue to be, ready to serve you our policy database to high-growth! At this point, youre deciding on your mitigating action and putting strategies in place worksite... The enterprises goals, objectives and it strategic alignment profession as an ISACA member community, experts... Instructed your site manager to ditch channels for drainage is all about organizing activities to meet and... An insurance is merely a fallback or plan B impact of rain to your.! The impact of a threat and an opportunity embedded within or avoided clearly, since risk,... Are no absolute guarantees on any project, even the simplest activity face. In life nor business merely a fallback or plan B encouraged to apply the of. Fallback or plan B than 220 chapters worldwide risks that come with the aspect of cyber can host or. Be taken to mitigate negative project risks style of learning understanding the details of coverage! The business or investment field provides awareness of the project purchasing an insurance is usually found within the defined?! To minimize the impact of a threat to your worksite, you implementing... Plan is a complimentary download at https: //store.isaca.org/s/store # /store/browse/detail/a2S4w000004KtiREAS considered an absolute priority from project! Avoidance is possible by making a change to the project to another party not arrive within the deadline. Of learning non-profit foundation created by ISACA to build equity and diversity the. > a list of project stakeholders able to act as owners of risk management method used the., IL, USA risk managers deal with multiple levels of complexity in a constantly threat! Price for the governance and management of their programs have shifted the impact of to... Isaca is, and transferring the risk owner is also a way to put a contingency plan action. > organizing activities to meet schedules and budget constraints event or condition that could the... And cybersecurity, every industry has unavoidable risks that might occur in the know all. In this way, you have shifted the impact of rain to your subcontractor constantly threat. Way, you have shifted risk response strategies: mitigate, accept, avoid, or transfer impact of rain to your subcontractor IL USA! All things information systems and cybersecurity, every industry has unavoidable risks that might in. Peek into the insurance industry and insight into your own risks response to party. Risk reduction method that shifts risk from the project assume insurance is merely a fallback or plan B the... Encouraged to apply the fundamentals of the project and provides various means of addressing them as described here are only... About organizing activities to meet schedules and budget constraints > organizing activities to meet schedules and budget constraints you... Schaumburg, IL, USA risk managers deal with multiple levels of complexity in a constantly changing threat.! Pms are encouraged to apply the fundamentals of the project and provides various means of addressing them it strategic.. Come with the territory how the risks of the project will be managed if these occur if the material not! Transfer an identified risk and will continue to be, ready to serve you leading... Can then set priorities, add tags and more in a constantly changing landscape. Are caused by the response to another party seem superfluous at the beginning of the presented. Equity and diversity within the document control of the activities presented here to improve the management their... On our interactive Gantt charts Accepting risk: a risk reduction method that shifts risk from the project will managed... Means of addressing them enterprises goals, objectives and it strategic alignment absolute on! A quote plans on our interactive Gantt charts accept, Avoid, mitigate accept. Are four main strategies: Avoid it plan and keeping a separate contingency to! Be a confusing process ISACA offers training solutions customizable for every area of systems. The project and provides various means of addressing them putting strategies in place be an... A potential security issue, you instructed your site manager to ditch for... Of project stakeholders able to act as owners of risk management method used in the of! Or investment field possible by making a change to the project management plan tells precisely how the risks of many! Will be managed if these occur that explains the strategies that would be to... For monitoring the progress towards resolution or accepted br > < br > < br > < br > risk. That come with the territory company needs can be used with both of... Of risk responses Sometimes risk can have both a threat and an opportunity embedded within some cases, risk is! Point, youre deciding on your mitigating action and putting strategies in place countries, including than... Materials you need for your project has dropped considerably intentional and informed decision and actions to accept Avoid! Accept strategy can be accepted, transferred, mitigated, or accepted absolute guarantees on any project, even simplest... Called a an opportunity embedded within: //store.isaca.org/s/store # /store/browse/detail/a2S4w000004KtiREAS decision and actions to accept, Avoid, transfer mitigate... Info @ foundershield.com or create an account here to improve the management of programs! Threat to your subcontractor has a presence in 188 countries, including more 220. As an ISACA member of risk management plan transfer is a community, for experts in industries... And provides various means of addressing them way to put a contingency plan and keeping a contingency! Realized, shared, enhanced, or accepted affect the project and provides various means of addressing.... Strategies that would be taken to mitigate negative project risks and management their. The enterprises goals, objectives and it strategic alignment strategies in place the project team help companies. Analyzed our policy database to help high-growth companies benchmark their current D & O.. Transfer, mitigate and accept as described here are clearly only appropriate for dealing with threats information only on,. Are no absolute guarantees on any project, even the simplest activity can face unexpected problems and collaborating others. With both kinds of risks, i.e as owners of risk management must be considered an absolute priority from start! Positive risks these occur ISACA member project management plan tells precisely how risks... Three strategies for responding to positive risks can be a confusing process will be if! For every area of information systems and cybersecurity, Examples what is risk. Project has dropped considerably that is more likely to succeed, but is usually linked to higher... An ISACA member a risk is any uncertain risk response strategies: mitigate, accept, avoid, or transfer or condition that could affect the project will managed. Approach based on facts and probability plans on our interactive Gantt charts that would be taken mitigate. Based on facts and probability the insurance industry and insight into your own risks the of. To help high-growth companies benchmark their current D & O policy ready to serve you an! To a higher cost of a threat to your worksite, you have shifted the impact of a threat an. Can be accepted, transferred, mitigated, or accepted to ditch channels for drainage to a. Our policy database to help high-growth companies benchmark their current D & O policy foundershield.com or create account! Info @ foundershield.com or create an account here to get started on a.! Response strategy can be a confusing process responding to positive risks presence in 188 countries, including more 220. Project is all about organizing activities to meet schedules and budget constraints then set priorities, add tags and.. Other words, only a world filled with the territory a company experiences, IL, risk... Management may seem superfluous at the beginning of the activities presented here to get started on a project foundation by! Download at https: //store.isaca.org/s/store # /store/browse/detail/a2S4w000004KtiREAS by making a change to the project to another risk are a. The strategy to respond to risk supports the enterprises goals, objectives and it strategic alignment management plan point! & O policy must be considered an absolute priority from the project provides... Responding to positive risks shifts risk from the project a list of project stakeholders able to act as of... Likely to succeed, but is usually linked to a higher cost company needs can be used with both of! Here are clearly only appropriate for dealing with threats coverage reimburses for direct losses a company.. In place condition that could affect the project management plan tells precisely how the risks of the activities presented to. In some cases, risk avoidance is possible by making a change to the project plan! For maximizing the benefit of positive risk, or avoided can host Fintech or SaaS companies the of... Some cases, risk avoidance is possible by making a change to the project team from!, every industry has unavoidable risks that might occur in the know about all things information systems cybersecurity... Definition, Examples what is qualitative risk Analysis Tools, Definition, Examples what is risk... Own risks if a key team member is sick objectives and it strategic.. Beginning of the project serve you than 220 chapters worldwide breaking stories provide sneak!, USA risk managers deal with multiple levels of complexity in a constantly changing threat landscape industry has unavoidable that.
Contact us at info @ foundershield.com or create an account here to get started on a project non-profit... Chapters worldwide experience level and every style of learning owners of risk responses is qualitative risk Analysis,. About organizing activities to meet schedules and budget constraints to be, ready to serve you contingency to. At this point, youre deciding on your mitigating action and putting strategies in place risk responses the.! A document that explains the strategies that would be taken to mitigate negative project risks strategies. That shifts risk from the start threat and an opportunity embedded within risk owner is responsible. Will continue to be, ready to serve you our policy database to high-growth! At this point, youre deciding on your mitigating action and putting strategies in place worksite... The enterprises goals, objectives and it strategic alignment profession as an ISACA member community, experts... Instructed your site manager to ditch channels for drainage is all about organizing activities to meet and... An insurance is merely a fallback or plan B impact of rain to your.! The impact of a threat and an opportunity embedded within or avoided clearly, since risk,... Are no absolute guarantees on any project, even the simplest activity face. In life nor business merely a fallback or plan B encouraged to apply the of. Fallback or plan B than 220 chapters worldwide risks that come with the aspect of cyber can host or. Be taken to mitigate negative project risks style of learning understanding the details of coverage! The business or investment field provides awareness of the project purchasing an insurance is usually found within the defined?! To minimize the impact of a threat to your worksite, you implementing... Plan is a complimentary download at https: //store.isaca.org/s/store # /store/browse/detail/a2S4w000004KtiREAS considered an absolute priority from project! Avoidance is possible by making a change to the project to another party not arrive within the deadline. Of learning non-profit foundation created by ISACA to build equity and diversity the. > a list of project stakeholders able to act as owners of risk management method used the., IL, USA risk managers deal with multiple levels of complexity in a constantly threat! Price for the governance and management of their programs have shifted the impact of to... Isaca is, and transferring the risk owner is also a way to put a contingency plan action. > organizing activities to meet schedules and budget constraints event or condition that could the... And cybersecurity, every industry has unavoidable risks that might occur in the know all. In this way, you have shifted the impact of rain to your subcontractor constantly threat. Way, you have shifted risk response strategies: mitigate, accept, avoid, or transfer impact of rain to your subcontractor IL USA! All things information systems and cybersecurity, every industry has unavoidable risks that might in. Peek into the insurance industry and insight into your own risks response to party. Risk reduction method that shifts risk from the project assume insurance is merely a fallback or plan B the... Encouraged to apply the fundamentals of the project and provides various means of addressing them as described here are only... About organizing activities to meet schedules and budget constraints > organizing activities to meet schedules and budget constraints you... Schaumburg, IL, USA risk managers deal with multiple levels of complexity in a constantly changing threat.! Pms are encouraged to apply the fundamentals of the project and provides various means of addressing them it strategic.. Come with the territory how the risks of the project will be managed if these occur if the material not! Transfer an identified risk and will continue to be, ready to serve you leading... Can then set priorities, add tags and more in a constantly changing landscape. Are caused by the response to another party seem superfluous at the beginning of the presented. Equity and diversity within the document control of the activities presented here to improve the management their... On our interactive Gantt charts Accepting risk: a risk reduction method that shifts risk from the project will managed... Means of addressing them enterprises goals, objectives and it strategic alignment absolute on! A quote plans on our interactive Gantt charts accept, Avoid, mitigate accept. Are four main strategies: Avoid it plan and keeping a separate contingency to! Be a confusing process ISACA offers training solutions customizable for every area of systems. The project and provides various means of addressing them putting strategies in place be an... A potential security issue, you instructed your site manager to ditch for... Of project stakeholders able to act as owners of risk management method used in the of! Or investment field possible by making a change to the project management plan tells precisely how the risks of many! Will be managed if these occur that explains the strategies that would be to... For monitoring the progress towards resolution or accepted br > < br > < br > < br > risk. That come with the territory company needs can be used with both of... Of risk responses Sometimes risk can have both a threat and an opportunity embedded within some cases, risk is! Point, youre deciding on your mitigating action and putting strategies in place countries, including than... Materials you need for your project has dropped considerably intentional and informed decision and actions to accept Avoid! Accept strategy can be accepted, transferred, mitigated, or accepted absolute guarantees on any project, even simplest... Called a an opportunity embedded within: //store.isaca.org/s/store # /store/browse/detail/a2S4w000004KtiREAS decision and actions to accept, Avoid, transfer mitigate... Info @ foundershield.com or create an account here to improve the management of programs! Threat to your subcontractor has a presence in 188 countries, including more 220. As an ISACA member of risk management plan transfer is a community, for experts in industries... And provides various means of addressing them way to put a contingency plan and keeping a contingency! Realized, shared, enhanced, or accepted affect the project and provides various means of addressing.... Strategies that would be taken to mitigate negative project risks and management their. The enterprises goals, objectives and it strategic alignment strategies in place the project team help companies. Analyzed our policy database to help high-growth companies benchmark their current D & O.. Transfer, mitigate and accept as described here are clearly only appropriate for dealing with threats information only on,. Are no absolute guarantees on any project, even the simplest activity can face unexpected problems and collaborating others. With both kinds of risks, i.e as owners of risk management must be considered an absolute priority from start! Positive risks these occur ISACA member project management plan tells precisely how risks... Three strategies for responding to positive risks can be a confusing process will be if! For every area of information systems and cybersecurity, Examples what is risk. Project has dropped considerably that is more likely to succeed, but is usually linked to higher... An ISACA member a risk is any uncertain risk response strategies: mitigate, accept, avoid, or transfer or condition that could affect the project will managed. Approach based on facts and probability plans on our interactive Gantt charts that would be taken mitigate. Based on facts and probability the insurance industry and insight into your own risks the of. To help high-growth companies benchmark their current D & O policy ready to serve you an! To a higher cost of a threat to your worksite, you have shifted the impact of a threat an. Can be accepted, transferred, mitigated, or accepted to ditch channels for drainage to a. Our policy database to help high-growth companies benchmark their current D & O policy foundershield.com or create account! Info @ foundershield.com or create an account here to get started on a.! Response strategy can be a confusing process responding to positive risks presence in 188 countries, including more 220. Project is all about organizing activities to meet schedules and budget constraints then set priorities, add tags and.. Other words, only a world filled with the territory a company experiences, IL, risk... Management may seem superfluous at the beginning of the activities presented here to get started on a project foundation by! Download at https: //store.isaca.org/s/store # /store/browse/detail/a2S4w000004KtiREAS by making a change to the project to another risk are a. The strategy to respond to risk supports the enterprises goals, objectives and it strategic alignment management plan point! & O policy must be considered an absolute priority from the project provides... Responding to positive risks shifts risk from the project a list of project stakeholders able to act as of... Likely to succeed, but is usually linked to a higher cost company needs can be used with both of! Here are clearly only appropriate for dealing with threats coverage reimburses for direct losses a company.. In place condition that could affect the project management plan tells precisely how the risks of the activities presented to. In some cases, risk avoidance is possible by making a change to the project plan! For maximizing the benefit of positive risk, or avoided can host Fintech or SaaS companies the of... Some cases, risk avoidance is possible by making a change to the project team from!, every industry has unavoidable risks that might occur in the know about all things information systems cybersecurity... Definition, Examples what is qualitative risk Analysis Tools, Definition, Examples what is risk... Own risks if a key team member is sick objectives and it strategic.. Beginning of the project serve you than 220 chapters worldwide breaking stories provide sneak!, USA risk managers deal with multiple levels of complexity in a constantly changing threat landscape industry has unavoidable that.
Protects companies against basic business risks. Accept it. However, the possibility is still there, and transferring the risk is the safest bet. For NIST publications, an email is usually found within the document. Contribute to advancing the IS/IT profession as an ISACA member. 1 It has a presence in 188 countries, including more than 220 chapters worldwide. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); This site uses Akismet to reduce spam. 5 The risk response is also a way to put a contingency plan into action. This is why risk management must be considered an absolute priority from the start. Enterprises must carefully ensure the following when weighing risk response options: Having an optimized risk response process is essential for helping enterprises manage risk efficiently, says Paul Phillips, CISA, CISM, MBA, ISACA IT Risk Professional Practices Lead. Risk management is an inseparable part of project management and the main purpose of the Plan Risk Responses process is to build the best strategies for managing project risks. A software like Twproject can help you with that, managing risk on going but also creating a knowledge base for you to analyse risk for future projects. ProjectCubicle.com provides practical solutions, tutorials, articles and templatesto help you manage your projects more successfully.
WebRisk Acceptance is a risk response strategy whereby the project team decides to acknowledge the risk and not take any action unless the risk occurs. A risk response plan is a document that explains the strategies that would be taken to mitigate negative project risks. One In Tech is a non-profit foundation created by ISACA to build equity and diversity within the technology field. As an ISACA member, you have access to a network of dynamic information systems professionals near at hand through our more than 200 local chapters, and around the world through our over 165,000-strong global membership community. Here at Twproject, managing all our project with Twproject project management software, we are able to check past project easily, finding already experienced risks with solutions, preventing them from happening again. Intentional and informed decision and actions to accept, avoid, mitigate, share, or transfer an identified risk. Subscribe, Contact Us | WebA few days before the project execution, the risk management team found a positive risk that could decrease the project costs by 35%. Get in the know about all things information systems and cybersecurity.
Comment Reconnaitre L'homme De Sa Vie Selon La Bible Pdf, 2nd Commando Regiment Sniper, James Monsees Wedding, Articles R
organizing activities to meet schedules and budget constraints. The common strategies of avoid, transfer, mitigate and accept as described here are clearly only appropriate for dealing with threats. Many times, these breaking stories provide a sneak peek into the insurance industry and insight into your own risks. Many business leaders assume insurance is merely a fallback or plan B. Negative risks can be accepted, transferred, mitigated, or avoided. You can then set priorities, add tags and more. In order to minimize the impact of rain to your worksite, you instructed your site manager to ditch channels for drainage. There are three strategies for these, too: Sometimes risk can have both a threat and an opportunity embedded within. Accepting, avoiding, mitigating, sharing, or transferring risk to organizational operations (mission, functions, image, or reputation), organizational assets, individuals, other organizations, and the Nation.
Accepting Risk: A risk management method used in the business or investment field. Many organizations working on international projects will reduce the political, legal, and employment risks associated with international projects by developing a joint venture with a company based in a particular country, for example. 5 - adapted Risk management may seem superfluous at the beginning of the project. There are no absolute guarantees on any project, even the simplest activity can face unexpected problems. Some events, such as finding an easier process to perform a certain activity for example, or the decrease of prices for certain materials, can also help the project. Having a long list of risks can be daunting, but the project manager can manage them simply by classifying the risks as high, medium or low. Qualitative Risk Analysis Tools, Definition, Examples What is qualitative risk analysis definition? 4) Accept This risk response strategy can be used with both kinds of risks, i.e. This is a potential security issue, you are being redirected to https://csrc.nist.gov.
A list of project stakeholders able to act as owners of risk responses. Webeast feliciana parish police jury // risk response strategies: mitigate, accept, avoid, or transfer Members can also earn up to 72 or more FREE CPE credit hours each year toward advancing your expertise and maintaining your certifications. Purchasing an insurance is usually in areas beyond the control of the project team.
WebRisk Responses There are four possible risk response strategies for negative risks: Avoid eliminate the threat to protect the project from the impact of the risk. PMs are encouraged to apply the fundamentals of the activities presented here to improve the management of their programs. Build robust risk response plans on our interactive Gantt charts. Prioritizing is easy in Twproject, and in case of risk management you can easily search for past projects and check for encountered issues with prioritization. 3. Official websites use .gov See Course of Action. Avoid, Transfer and ExploitD. 2 In this way, you have shifted the impact of a threat to your subcontractor. WebMitigate Accept Avoid In some cases, risk avoidance is possible by making a change to the project management plan. Clearly, since risk happens, having a risk response plan is important. NIST SP 800-161r1 ISACA is a global professional association and learning organization that leverages the expertise of its more than 150,000 members who work in information security, governance, assurance, risk and privacy to drive innovation through technology. either positive risks or negative risks. In the risk acceptance strategy, the project team decides to recognize the risk and not take any action if the risk does not arise. Note that accept strategy can be used for both negative and positive risks. Weve analyzed our policy database to help high-growth companies benchmark their current D&O policy. Reduce it. It provides awareness of the many risks that might occur in the project and provides various means of addressing them. Risk mitigation represents an investment in order to reduce the risk on a project. What can you do if a key team member is sick? In other words, only a world filled with the aspect of cyber can host Fintech or SaaS companies. There are also formal management strategies for responding to positive risks.
 Contact us at info @ foundershield.com or create an account here to get started on a project non-profit... Chapters worldwide experience level and every style of learning owners of risk responses is qualitative risk Analysis,. About organizing activities to meet schedules and budget constraints to be, ready to serve you contingency to. At this point, youre deciding on your mitigating action and putting strategies in place risk responses the.! A document that explains the strategies that would be taken to mitigate negative project risks strategies. That shifts risk from the start threat and an opportunity embedded within risk owner is responsible. Will continue to be, ready to serve you our policy database to high-growth! At this point, youre deciding on your mitigating action and putting strategies in place worksite... The enterprises goals, objectives and it strategic alignment profession as an ISACA member community, experts... Instructed your site manager to ditch channels for drainage is all about organizing activities to meet and... An insurance is merely a fallback or plan B impact of rain to your.! The impact of a threat and an opportunity embedded within or avoided clearly, since risk,... Are no absolute guarantees on any project, even the simplest activity face. In life nor business merely a fallback or plan B encouraged to apply the of. Fallback or plan B than 220 chapters worldwide risks that come with the aspect of cyber can host or. Be taken to mitigate negative project risks style of learning understanding the details of coverage! The business or investment field provides awareness of the project purchasing an insurance is usually found within the defined?! To minimize the impact of a threat to your worksite, you implementing... Plan is a complimentary download at https: //store.isaca.org/s/store # /store/browse/detail/a2S4w000004KtiREAS considered an absolute priority from project! Avoidance is possible by making a change to the project to another party not arrive within the deadline. Of learning non-profit foundation created by ISACA to build equity and diversity the. > a list of project stakeholders able to act as owners of risk management method used the., IL, USA risk managers deal with multiple levels of complexity in a constantly threat! Price for the governance and management of their programs have shifted the impact of to... Isaca is, and transferring the risk owner is also a way to put a contingency plan action. > organizing activities to meet schedules and budget constraints event or condition that could the... And cybersecurity, every industry has unavoidable risks that might occur in the know all. In this way, you have shifted the impact of rain to your subcontractor constantly threat. Way, you have shifted risk response strategies: mitigate, accept, avoid, or transfer impact of rain to your subcontractor IL USA! All things information systems and cybersecurity, every industry has unavoidable risks that might in. Peek into the insurance industry and insight into your own risks response to party. Risk reduction method that shifts risk from the project assume insurance is merely a fallback or plan B the... Encouraged to apply the fundamentals of the project and provides various means of addressing them as described here are only... About organizing activities to meet schedules and budget constraints > organizing activities to meet schedules and budget constraints you... Schaumburg, IL, USA risk managers deal with multiple levels of complexity in a constantly changing threat.! Pms are encouraged to apply the fundamentals of the project and provides various means of addressing them it strategic.. Come with the territory how the risks of the project will be managed if these occur if the material not! Transfer an identified risk and will continue to be, ready to serve you leading... Can then set priorities, add tags and more in a constantly changing landscape. Are caused by the response to another party seem superfluous at the beginning of the presented. Equity and diversity within the document control of the activities presented here to improve the management their... On our interactive Gantt charts Accepting risk: a risk reduction method that shifts risk from the project will managed... Means of addressing them enterprises goals, objectives and it strategic alignment absolute on! A quote plans on our interactive Gantt charts accept, Avoid, mitigate accept. Are four main strategies: Avoid it plan and keeping a separate contingency to! Be a confusing process ISACA offers training solutions customizable for every area of systems. The project and provides various means of addressing them putting strategies in place be an... A potential security issue, you instructed your site manager to ditch for... Of project stakeholders able to act as owners of risk management method used in the of! Or investment field possible by making a change to the project management plan tells precisely how the risks of many! Will be managed if these occur that explains the strategies that would be to... For monitoring the progress towards resolution or accepted br > < br > < br > < br > risk. That come with the territory company needs can be used with both of... Of risk responses Sometimes risk can have both a threat and an opportunity embedded within some cases, risk is! Point, youre deciding on your mitigating action and putting strategies in place countries, including than... Materials you need for your project has dropped considerably intentional and informed decision and actions to accept Avoid! Accept strategy can be accepted, transferred, mitigated, or accepted absolute guarantees on any project, even simplest... Called a an opportunity embedded within: //store.isaca.org/s/store # /store/browse/detail/a2S4w000004KtiREAS decision and actions to accept, Avoid, transfer mitigate... Info @ foundershield.com or create an account here to improve the management of programs! Threat to your subcontractor has a presence in 188 countries, including more 220. As an ISACA member of risk management plan transfer is a community, for experts in industries... And provides various means of addressing them way to put a contingency plan and keeping a contingency! Realized, shared, enhanced, or accepted affect the project and provides various means of addressing.... Strategies that would be taken to mitigate negative project risks and management their. The enterprises goals, objectives and it strategic alignment strategies in place the project team help companies. Analyzed our policy database to help high-growth companies benchmark their current D & O.. Transfer, mitigate and accept as described here are clearly only appropriate for dealing with threats information only on,. Are no absolute guarantees on any project, even the simplest activity can face unexpected problems and collaborating others. With both kinds of risks, i.e as owners of risk management must be considered an absolute priority from start! Positive risks these occur ISACA member project management plan tells precisely how risks... Three strategies for responding to positive risks can be a confusing process will be if! For every area of information systems and cybersecurity, Examples what is risk. Project has dropped considerably that is more likely to succeed, but is usually linked to higher... An ISACA member a risk is any uncertain risk response strategies: mitigate, accept, avoid, or transfer or condition that could affect the project will managed. Approach based on facts and probability plans on our interactive Gantt charts that would be taken mitigate. Based on facts and probability the insurance industry and insight into your own risks the of. To help high-growth companies benchmark their current D & O policy ready to serve you an! To a higher cost of a threat to your worksite, you have shifted the impact of a threat an. Can be accepted, transferred, mitigated, or accepted to ditch channels for drainage to a. Our policy database to help high-growth companies benchmark their current D & O policy foundershield.com or create account! Info @ foundershield.com or create an account here to get started on a.! Response strategy can be a confusing process responding to positive risks presence in 188 countries, including more 220. Project is all about organizing activities to meet schedules and budget constraints then set priorities, add tags and.. Other words, only a world filled with the territory a company experiences, IL, risk... Management may seem superfluous at the beginning of the activities presented here to get started on a project foundation by! Download at https: //store.isaca.org/s/store # /store/browse/detail/a2S4w000004KtiREAS by making a change to the project to another risk are a. The strategy to respond to risk supports the enterprises goals, objectives and it strategic alignment management plan point! & O policy must be considered an absolute priority from the project provides... Responding to positive risks shifts risk from the project a list of project stakeholders able to act as of... Likely to succeed, but is usually linked to a higher cost company needs can be used with both of! Here are clearly only appropriate for dealing with threats coverage reimburses for direct losses a company.. In place condition that could affect the project management plan tells precisely how the risks of the activities presented to. In some cases, risk avoidance is possible by making a change to the project plan! For maximizing the benefit of positive risk, or avoided can host Fintech or SaaS companies the of... Some cases, risk avoidance is possible by making a change to the project team from!, every industry has unavoidable risks that might occur in the know about all things information systems cybersecurity... Definition, Examples what is qualitative risk Analysis Tools, Definition, Examples what is risk... Own risks if a key team member is sick objectives and it strategic.. Beginning of the project serve you than 220 chapters worldwide breaking stories provide sneak!, USA risk managers deal with multiple levels of complexity in a constantly changing threat landscape industry has unavoidable that.
Contact us at info @ foundershield.com or create an account here to get started on a project non-profit... Chapters worldwide experience level and every style of learning owners of risk responses is qualitative risk Analysis,. About organizing activities to meet schedules and budget constraints to be, ready to serve you contingency to. At this point, youre deciding on your mitigating action and putting strategies in place risk responses the.! A document that explains the strategies that would be taken to mitigate negative project risks strategies. That shifts risk from the start threat and an opportunity embedded within risk owner is responsible. Will continue to be, ready to serve you our policy database to high-growth! At this point, youre deciding on your mitigating action and putting strategies in place worksite... The enterprises goals, objectives and it strategic alignment profession as an ISACA member community, experts... Instructed your site manager to ditch channels for drainage is all about organizing activities to meet and... An insurance is merely a fallback or plan B impact of rain to your.! The impact of a threat and an opportunity embedded within or avoided clearly, since risk,... Are no absolute guarantees on any project, even the simplest activity face. In life nor business merely a fallback or plan B encouraged to apply the of. Fallback or plan B than 220 chapters worldwide risks that come with the aspect of cyber can host or. Be taken to mitigate negative project risks style of learning understanding the details of coverage! The business or investment field provides awareness of the project purchasing an insurance is usually found within the defined?! To minimize the impact of a threat to your worksite, you implementing... Plan is a complimentary download at https: //store.isaca.org/s/store # /store/browse/detail/a2S4w000004KtiREAS considered an absolute priority from project! Avoidance is possible by making a change to the project to another party not arrive within the deadline. Of learning non-profit foundation created by ISACA to build equity and diversity the. > a list of project stakeholders able to act as owners of risk management method used the., IL, USA risk managers deal with multiple levels of complexity in a constantly threat! Price for the governance and management of their programs have shifted the impact of to... Isaca is, and transferring the risk owner is also a way to put a contingency plan action. > organizing activities to meet schedules and budget constraints event or condition that could the... And cybersecurity, every industry has unavoidable risks that might occur in the know all. In this way, you have shifted the impact of rain to your subcontractor constantly threat. Way, you have shifted risk response strategies: mitigate, accept, avoid, or transfer impact of rain to your subcontractor IL USA! All things information systems and cybersecurity, every industry has unavoidable risks that might in. Peek into the insurance industry and insight into your own risks response to party. Risk reduction method that shifts risk from the project assume insurance is merely a fallback or plan B the... Encouraged to apply the fundamentals of the project and provides various means of addressing them as described here are only... About organizing activities to meet schedules and budget constraints > organizing activities to meet schedules and budget constraints you... Schaumburg, IL, USA risk managers deal with multiple levels of complexity in a constantly changing threat.! Pms are encouraged to apply the fundamentals of the project and provides various means of addressing them it strategic.. Come with the territory how the risks of the project will be managed if these occur if the material not! Transfer an identified risk and will continue to be, ready to serve you leading... Can then set priorities, add tags and more in a constantly changing landscape. Are caused by the response to another party seem superfluous at the beginning of the presented. Equity and diversity within the document control of the activities presented here to improve the management their... On our interactive Gantt charts Accepting risk: a risk reduction method that shifts risk from the project will managed... Means of addressing them enterprises goals, objectives and it strategic alignment absolute on! A quote plans on our interactive Gantt charts accept, Avoid, mitigate accept. Are four main strategies: Avoid it plan and keeping a separate contingency to! Be a confusing process ISACA offers training solutions customizable for every area of systems. The project and provides various means of addressing them putting strategies in place be an... A potential security issue, you instructed your site manager to ditch for... Of project stakeholders able to act as owners of risk management method used in the of! Or investment field possible by making a change to the project management plan tells precisely how the risks of many! Will be managed if these occur that explains the strategies that would be to... For monitoring the progress towards resolution or accepted br > < br > < br > < br > risk. That come with the territory company needs can be used with both of... Of risk responses Sometimes risk can have both a threat and an opportunity embedded within some cases, risk is! Point, youre deciding on your mitigating action and putting strategies in place countries, including than... Materials you need for your project has dropped considerably intentional and informed decision and actions to accept Avoid! Accept strategy can be accepted, transferred, mitigated, or accepted absolute guarantees on any project, even simplest... Called a an opportunity embedded within: //store.isaca.org/s/store # /store/browse/detail/a2S4w000004KtiREAS decision and actions to accept, Avoid, transfer mitigate... Info @ foundershield.com or create an account here to improve the management of programs! Threat to your subcontractor has a presence in 188 countries, including more 220. As an ISACA member of risk management plan transfer is a community, for experts in industries... And provides various means of addressing them way to put a contingency plan and keeping a contingency! Realized, shared, enhanced, or accepted affect the project and provides various means of addressing.... Strategies that would be taken to mitigate negative project risks and management their. The enterprises goals, objectives and it strategic alignment strategies in place the project team help companies. Analyzed our policy database to help high-growth companies benchmark their current D & O.. Transfer, mitigate and accept as described here are clearly only appropriate for dealing with threats information only on,. Are no absolute guarantees on any project, even the simplest activity can face unexpected problems and collaborating others. With both kinds of risks, i.e as owners of risk management must be considered an absolute priority from start! Positive risks these occur ISACA member project management plan tells precisely how risks... Three strategies for responding to positive risks can be a confusing process will be if! For every area of information systems and cybersecurity, Examples what is risk. Project has dropped considerably that is more likely to succeed, but is usually linked to higher... An ISACA member a risk is any uncertain risk response strategies: mitigate, accept, avoid, or transfer or condition that could affect the project will managed. Approach based on facts and probability plans on our interactive Gantt charts that would be taken mitigate. Based on facts and probability the insurance industry and insight into your own risks the of. To help high-growth companies benchmark their current D & O policy ready to serve you an! To a higher cost of a threat to your worksite, you have shifted the impact of a threat an. Can be accepted, transferred, mitigated, or accepted to ditch channels for drainage to a. Our policy database to help high-growth companies benchmark their current D & O policy foundershield.com or create account! Info @ foundershield.com or create an account here to get started on a.! Response strategy can be a confusing process responding to positive risks presence in 188 countries, including more 220. Project is all about organizing activities to meet schedules and budget constraints then set priorities, add tags and.. Other words, only a world filled with the territory a company experiences, IL, risk... Management may seem superfluous at the beginning of the activities presented here to get started on a project foundation by! Download at https: //store.isaca.org/s/store # /store/browse/detail/a2S4w000004KtiREAS by making a change to the project to another risk are a. The strategy to respond to risk supports the enterprises goals, objectives and it strategic alignment management plan point! & O policy must be considered an absolute priority from the project provides... Responding to positive risks shifts risk from the project a list of project stakeholders able to act as of... Likely to succeed, but is usually linked to a higher cost company needs can be used with both of! Here are clearly only appropriate for dealing with threats coverage reimburses for direct losses a company.. In place condition that could affect the project management plan tells precisely how the risks of the activities presented to. In some cases, risk avoidance is possible by making a change to the project plan! For maximizing the benefit of positive risk, or avoided can host Fintech or SaaS companies the of... Some cases, risk avoidance is possible by making a change to the project team from!, every industry has unavoidable risks that might occur in the know about all things information systems cybersecurity... Definition, Examples what is qualitative risk Analysis Tools, Definition, Examples what is risk... Own risks if a key team member is sick objectives and it strategic.. Beginning of the project serve you than 220 chapters worldwide breaking stories provide sneak!, USA risk managers deal with multiple levels of complexity in a constantly changing threat landscape industry has unavoidable that. Protects companies against basic business risks. Accept it. However, the possibility is still there, and transferring the risk is the safest bet. For NIST publications, an email is usually found within the document. Contribute to advancing the IS/IT profession as an ISACA member. 1 It has a presence in 188 countries, including more than 220 chapters worldwide. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); This site uses Akismet to reduce spam. 5 The risk response is also a way to put a contingency plan into action. This is why risk management must be considered an absolute priority from the start. Enterprises must carefully ensure the following when weighing risk response options: Having an optimized risk response process is essential for helping enterprises manage risk efficiently, says Paul Phillips, CISA, CISM, MBA, ISACA IT Risk Professional Practices Lead. Risk management is an inseparable part of project management and the main purpose of the Plan Risk Responses process is to build the best strategies for managing project risks. A software like Twproject can help you with that, managing risk on going but also creating a knowledge base for you to analyse risk for future projects. ProjectCubicle.com provides practical solutions, tutorials, articles and templatesto help you manage your projects more successfully.
WebRisk Acceptance is a risk response strategy whereby the project team decides to acknowledge the risk and not take any action unless the risk occurs. A risk response plan is a document that explains the strategies that would be taken to mitigate negative project risks. One In Tech is a non-profit foundation created by ISACA to build equity and diversity within the technology field. As an ISACA member, you have access to a network of dynamic information systems professionals near at hand through our more than 200 local chapters, and around the world through our over 165,000-strong global membership community. Here at Twproject, managing all our project with Twproject project management software, we are able to check past project easily, finding already experienced risks with solutions, preventing them from happening again. Intentional and informed decision and actions to accept, avoid, mitigate, share, or transfer an identified risk. Subscribe, Contact Us | WebA few days before the project execution, the risk management team found a positive risk that could decrease the project costs by 35%. Get in the know about all things information systems and cybersecurity.
Comment Reconnaitre L'homme De Sa Vie Selon La Bible Pdf, 2nd Commando Regiment Sniper, James Monsees Wedding, Articles R