Read now: https://lnkd.in/dANpTXAR Download now: https://lnkd.in/dAxwf7xX #superchargingprogress #microsoftdefender #endpointprotection #DynamicCybersecurity, Download the case study to know how we supercharged the existing security architecture and enhanced the overall security posture for a fortune 500 healthcare giant using our IAM and endpoint security solutions.
Texeira headed a presentation on how cloud infrastructure entitlement management (CIEM) and identity threat detection and response (ITDR) can enhance security posture management. maintain an IGA solution. In a world powered by cloud computing, every human and machine identity, whether it exists on-premises or in the cloud, needs to be protected to prevent a breach. Omada is a Platinum
This again is why Ransomware Containment and not just detection should be central to your strategy: WebWith IAM orchestration, security teams can increase transparency over authentication while also minimizing friction for end users. via VentureBeat. Intelligent compliance 20 22 March 2023 | Gaylord Texan Hotel & Convention Center, Grapevine,Texas, US. Thank you Anoosh Saboori for getting the blogpost published and for speaking about all the work we do to keep our customers safe. and Administration best practices. This can lead to better user retention and a stronger reputation for the company or organization providing the security tools.
Whether or not you made it to the conference, you can see our sessions on demand!The challenges faced by employers with remote workforces are continuing to evolve - from building and system access, to identity verification, to enhancing security measures. Gartner Paul Jarratt on LinkedIn: 4 key trends from the Gartner IAM Summit 2023 Please be advised that in the conference industry we often come across fraudulent service providers that claim to be able to offer hotel reservation services. Considering the European Unions leading role in the development of modern data and privacy regulations and the arrival of several US states in the privacy regulations map, here are some of the things we will be following with close attention in 2023. Prashant Mascarenhas Sanjay Karandikar Sonal Srivastava Bobby Singh Mukesh Dubey Compounding the problem is that popular new tools like GraphQL do not have security built-in to them and cloud-native apps have inconsistently built features like token exchanges. Choose Use These networks can be easily compromised, leaving your data vulnerable to theft. I talked about the threat against business and people, plus a view into the future with GPT. Given its prominence in many presentations and discussions, its evident that Runtime Authorization will become the new standard for the identity strategy of companies with leading security practices. #GRC 3. WebShow Identity at the Center, Ep #205 - 2023 Gartner US IAM Summit Review - Mar 27, 2023 Reminiscing about the 80s is fun. ForgeRock Enterprise Connect Passwordless helps you do just that. Over 80% of organizations have suffered an identity-related breach in the last 12 months.. #microsoftsecurity This security-specific model incorporates a growing set of security-specific skills and is informed by Microsoft's unique global threat intelligence and more than 65 trillion daily signals. Best-practice framework for solution design and deployment, High degree of configurability
Because i dentity is the front door to your enterprise, enabling secure connections with your customers and workforce. With Security Copilot, we are building a future where every defender is empowered with the technologies and expertise that enable them to reach their full potential. 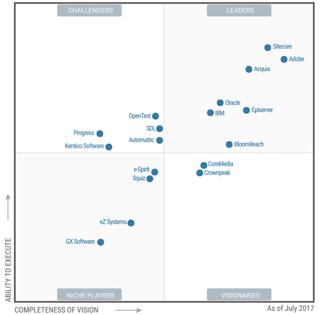 Everyone can and will be fooled, it is therefore important to have that as a clear mindset when working with people, and from there enterprise security. Read this blog to know the best practices, important principles and practical insights on compliance. Took everyone through the obvious MFA talk and encouraged everyone to implement it for as much as they could, plus telling the same to family, kids and friend. Gartner senior director analyst Rebecca Archambault believes that by 2026, 70% of identity-first security strategies will fail unless organizations adopt context-based access policies that are continuous and consistent. As professionals, let's lead by example and encourage our networks to adopt best practices in cybersecurity. While there are tools to scan the files for malware, there is no automated way to make sure that the data contained in the database is accurate and, even more importantly, was obtained with proper consent. Lots of great sessions and discussions with a number of folks. Atul Outdated software: Keep your devices updated with the latest security patches and antivirus software to protect against known vulnerabilities. Join top executives in San Francisco on July 11-12, to hear how leaders are integrating and optimizing AI investments for success. #AI #TI #cybersecurity will never be the same
Everyone can and will be fooled, it is therefore important to have that as a clear mindset when working with people, and from there enterprise security. Read this blog to know the best practices, important principles and practical insights on compliance. Took everyone through the obvious MFA talk and encouraged everyone to implement it for as much as they could, plus telling the same to family, kids and friend. Gartner senior director analyst Rebecca Archambault believes that by 2026, 70% of identity-first security strategies will fail unless organizations adopt context-based access policies that are continuous and consistent. As professionals, let's lead by example and encourage our networks to adopt best practices in cybersecurity. While there are tools to scan the files for malware, there is no automated way to make sure that the data contained in the database is accurate and, even more importantly, was obtained with proper consent. Lots of great sessions and discussions with a number of folks. Atul Outdated software: Keep your devices updated with the latest security patches and antivirus software to protect against known vulnerabilities. Join top executives in San Francisco on July 11-12, to hear how leaders are integrating and optimizing AI investments for success. #AI #TI #cybersecurity will never be the same  For more information, check out the blog below!
For more information, check out the blog below!
Please have a look. Phishing scams: Be cautious of emails that appear to be from tax agencies or financial institutions. Omada is pleased to be named a
Identity is the new network perimeter. 0:00. To enhance cyberattack preparedness, security and risk management leaders must add identity threat detection and response capabilities to their security infrastructure, Texeira said. Least privilege and separation of duties policies
As part of this transformation, the Identity and Access Management (IAM) program was revamped to support the ongoing DevOps maintenance of both the enterprise and partner #identity platforms. Fill out the form below and we'll schedule time for a personal demo. Check out an official announcement in the bog https://lnkd.in/gQ8ju9tt #sharingiscaring  Learn how we showcase our products' capabilities. Prashant Mascarenhas Deepak Nawani Saurabh Chanpuria Sreekumar S (FIE) Sanjay Karandikar
Learn how we showcase our products' capabilities. Prashant Mascarenhas Deepak Nawani Saurabh Chanpuria Sreekumar S (FIE) Sanjay Karandikar 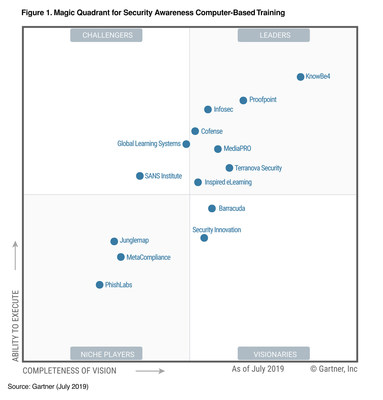 Zero Trust soldier, working to change and enhance. Download Julianna Nijmeh su LinkedIn: 4 key trends from the Gartner IAM Summit 2023 WebIt was great to see access management take center stage in the Gartner IAM conference this year.
Zero Trust soldier, working to change and enhance. Download Julianna Nijmeh su LinkedIn: 4 key trends from the Gartner IAM Summit 2023 WebIt was great to see access management take center stage in the Gartner IAM conference this year. ![]()
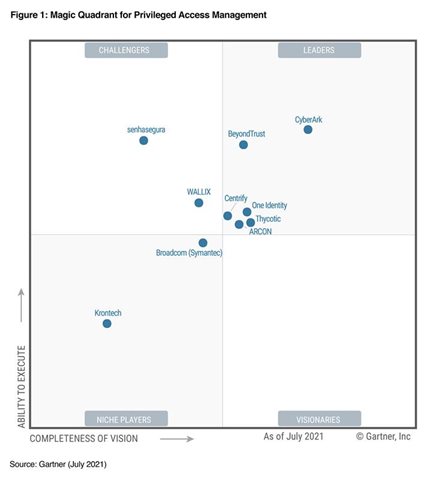 Security professionals are scarce, and we must empower them to disrupt attackers' traditional advantages and drive innovation for their organizations. The strings within the ransomware are encrypted, which is likely done to make it harder for defenders to create a generic detection rule. Organizations that want to build a secure identity fabric will inevitably need to rely on technologies like CIEM. 3/20/2023. Download to know more: https://lnkd.in/dncw-fS2
Security professionals are scarce, and we must empower them to disrupt attackers' traditional advantages and drive innovation for their organizations. The strings within the ransomware are encrypted, which is likely done to make it harder for defenders to create a generic detection rule. Organizations that want to build a secure identity fabric will inevitably need to rely on technologies like CIEM. 3/20/2023. Download to know more: https://lnkd.in/dncw-fS2  SailPoint's Non-Employee Risk Management solution enables organizations to execute risk-based identity access and lifecycle strategies for their entire population of non-employees. And timely enough, we just launched the SailPoint Non-Employee Risk Management solution to fill this gap. Security Copilot combines the most advanced large language model (LLM) with a security-specific model from Microsoft. Artin AvanesChristian KleinermanMario DuarteMatthew RoseJacob S.Iulia IonCameron TekiyehBenoit DagevilleOmer SingerJosh KlahrMichele FreschiFrantiek RolinekPrasoon ShuklaZheng Mi , Chief Technology Officer, Microsoft Worldwide Defense & Intelligence | Keynote Speaker | Board Member | Top 100 Women in Tech, Today, we are delighted to introduce Microsoft Security Copilot and welcome you to the new era of #security shaped by the power of OpenAIs #GPT4 #generativeAI. Multi-Factor Authentication US Army veteran and results driven technical leader with 20+ years of progressive leadership in network and security technology management across telecom, manufacturing, and financial services industries. Recently, VentureBeat spoke to some of the top Gartner analysts presenting at the event. VentureBeat shares the top takeaways for enterprises from #GartnerIAM. He delivers authentication, authorization, data protection, security architecture, user lifecycle management, and system to system integration controls services across the organization. Gartner Identity & Access Management Summit 2023helps IAM and security leaders make the right decisions about which identity-first security initiatives to prioritize, how to modernize existing staffing models and whether to invest in new tools to take their organizations security posture into the identity-first era. #ransomware https://lnkd.in/gYEDRhrV, Security Professional | Security Consultant | Speaker | Advisor | Masters Candidate, As we dive headfirst into tax season, it's crucial for you and your family members to stay vigilant about cybersecurity risks that tend to spike during this time of the year. WebOur team had a wonderful time at the two-day Gartner IAM 2023 Summit in Texas.
SailPoint's Non-Employee Risk Management solution enables organizations to execute risk-based identity access and lifecycle strategies for their entire population of non-employees. And timely enough, we just launched the SailPoint Non-Employee Risk Management solution to fill this gap. Security Copilot combines the most advanced large language model (LLM) with a security-specific model from Microsoft. Artin AvanesChristian KleinermanMario DuarteMatthew RoseJacob S.Iulia IonCameron TekiyehBenoit DagevilleOmer SingerJosh KlahrMichele FreschiFrantiek RolinekPrasoon ShuklaZheng Mi , Chief Technology Officer, Microsoft Worldwide Defense & Intelligence | Keynote Speaker | Board Member | Top 100 Women in Tech, Today, we are delighted to introduce Microsoft Security Copilot and welcome you to the new era of #security shaped by the power of OpenAIs #GPT4 #generativeAI. Multi-Factor Authentication US Army veteran and results driven technical leader with 20+ years of progressive leadership in network and security technology management across telecom, manufacturing, and financial services industries. Recently, VentureBeat spoke to some of the top Gartner analysts presenting at the event. VentureBeat shares the top takeaways for enterprises from #GartnerIAM. He delivers authentication, authorization, data protection, security architecture, user lifecycle management, and system to system integration controls services across the organization. Gartner Identity & Access Management Summit 2023helps IAM and security leaders make the right decisions about which identity-first security initiatives to prioritize, how to modernize existing staffing models and whether to invest in new tools to take their organizations security posture into the identity-first era. #ransomware https://lnkd.in/gYEDRhrV, Security Professional | Security Consultant | Speaker | Advisor | Masters Candidate, As we dive headfirst into tax season, it's crucial for you and your family members to stay vigilant about cybersecurity risks that tend to spike during this time of the year. WebOur team had a wonderful time at the two-day Gartner IAM 2023 Summit in Texas.
3. The complete list of regulated entities that are impacted by KYC requirements varies from one country to another. March 27, 2023 Follow us In his closing keynote, Gartner Vice President Homan Farahmand summarized the outlook for identity and access management by While it is challenging to sort through all the amazing content presented and discussed at the conference, SGNLers Atul Tulshibagwale and Kristen Ditsch have summarized 5 Key Takeaways that you must not miss. Vasu Jakkal and C. Kelly Bissell , thank you and the team on this new and innovative take that I truly hope will blaze the trail.. AWS | Modern Marketing | New Business Development | Cloud | Artificial Intelligence | Partnerships, Newly launched, the AWS Security Partner Resources page built for customers! Combat traditional MFA challenges with a new Event Transform 2023 Join us in San Francisco on July 11-12, where top executives will share how they have integrated and optimized AI investments for success 2023 will be the year when several new regulations take effect but we can also expect even more new regulations to be adopted. RegisterNow, InterContinental London The O2 Security Copilot leverages a large language model (#LLM), a security-specific model from Microsoft, and our unique global threat intelligence with more than 65 trillion daily signals. JimandJefftalk about their experiences at the 2023 Gartner US IAM Summit.More takeaways from the conference: https://venturebeat.com/security/4-key-trends-from-the-gartner-iam-summit-2023/Identiverse: https://identiverse.com/Use our discount code for 20% off your Identiverse registration: IDV-ICEN23Connect with us on LinkedIn:Jim McDonald:https://www.linkedin.com/in/jimmcdonaldpmp/Jeff Steadman:https://www.linkedin.com/in/jeffsteadman/Visit the show on the web at idacpodcast.com and follow@IDACPodcaston Twitter. Reduces mistakes: When security tools are user-friendly, people are less likely to make mistakes that could put their information at risk. Identity fabric immunity applies the concept of digital immune systems to identity infrastructure to minimize defects and failures, Texeira said. So, in short, Security Copilot is not only a large language model, but rather a system that learns, to enable organizations to truly defend against #cyber threats at machine speed. Scammers often use these disguises to trick you into clicking on malicious links or revealing personal information. While ransomware attacks in hospitals have not been in the news lately, the threat is still there. Meanwhile, in Europe, KYC and AML are governed by the AMLD regulations. Dozens of out-of-the-box connectors
This is just one of the many cyber threats that impact organizations worldwide, making it hard to keep up with the current and evolving security landscape. #microsoftazure#MSSecure#microsoftsecurity#copilot #microsoftsecure#cloudsecurity#securityposture#management#cloudengineers#cloudarchitects#linkedinfamily#cloudfamily#securityengineers#alwayslearning, Information Security | Cloud Security-0365,CASB,Azure | CyberArk | Tripwire| Splunk, Data Security in the Cloud Microsoft Defender #ThreatIntelligence is now available to licensed customers directly within #M365Defender. Gartner Paul Jarratt on LinkedIn: 4 key trends from the Gartner IAM Summit 2023 Another key value it brings is to help drive revenue impact as an enabler for digital transformation. This new contract is called out as a pillar in the recent White House cybersecurity strategy publication. WebIt was great to see access management take center stage in the Gartner IAM conference this year. WebGartner senior director analyst Rebecca Archambault believes that by 2026, 70% of identity-first security strategies will fail unless organizations adopt Hansel Trejo on LinkedIn: 4 key trends from the Gartner IAM Summit 2023 A few general observations on how these trends shape up with my own Venkat Raghavan on LinkedIn: 4 key trends from the Gartner IAM Summit 2023 As businesses continue their digital transformations and become increasingly cloud-based and adopt zero-trust architectures, security teams face a growing threat landscape. #opentowork, Using dark web intelligence to protect Microsoft and our customers, One door closes, when another one opens. Listen to the full conversation between Steven Edwards, John Vecchi and Brian Contos over on the #IoTSecurity Podcast, powered by Phosphorus Cybersecurity Inc. https://okt.to/jkPdRf, Sr. Cyber Security Technical Specialist at Microsoft, BOOM! We met a lot of great people, and had some interesting conversations about the challenges in the identity and access management space. Fill out the form to book a meeting with us. Use automatically extracted and verified data to fill users profiles, ensuring accuracy, speed, and a seamless user experience. Cyber attacks take out EHRs for weeks and most downtime plans don't scale. Webhttps://lnkd.in/g3KK2T26 Good read on the top trends from the Gartner IAM Summit. Prioritize employee trust and privacy The conference program has been scheduled to cover as many time zones as possible to support attendance from our members and our wider asset management community from across the world. If you're like me, you feel that seeing is believing. Join Jason Murphy, Sr. Director of Network and Security Services from Donnelly Financial Solutions, and Tye McGlynn, Director of IAM at Guidewire Software, for a panel discussion on how to approach, deploy, and scale an IGA program. WebGartner Identity & Access Management Summit 2023 helps IAM and security leaders make the right decisions about which identity-first security initiatives to prioritize, how to modernize existing staffing models and whether to invest in new tools to take their organizations security posture into the identity-first era. Knowledge-sharing Community, Ensure fast and successful IGA deployment
Explore the 2023 Gartner Identity & Access Management Summit agenda, conference features and networking opportunities. For Akif Khan, VP analyst at Gartner, organizations need to find a way to harmonize the user journey, which combines identity proofing, authentication, access management and fraud detection, into a cohesive whole.  In a world powered by #cloudcomputing, every human and machine identity, whether it exists on-premises or in the cloud Want to learn how SGNL could protect your organization?
In a world powered by #cloudcomputing, every human and machine identity, whether it exists on-premises or in the cloud Want to learn how SGNL could protect your organization?  Automates access provisioning and enables the workforce from day 1, Automated access provisioning and deprovisioning
From learning best practices in track sessions to connecting with peers and experts during interactive experiences, the event provided an excellent opportunity to discover new ways and solutions in the #IAM space and understand pressing customer challenges. Yet the Gartner IAM Summit, which began yesterday in Grapevine, Texas, highlights that most organizations still have a long way to go.
Automates access provisioning and enables the workforce from day 1, Automated access provisioning and deprovisioning
From learning best practices in track sessions to connecting with peers and experts during interactive experiences, the event provided an excellent opportunity to discover new ways and solutions in the #IAM space and understand pressing customer challenges. Yet the Gartner IAM Summit, which began yesterday in Grapevine, Texas, highlights that most organizations still have a long way to go.  Security Copilot combines this advanced large language model (LLM) with a security-specific model from Microsoft. If security initiatives are hard to use or confusing, people might not use them properly, which leads to security risks. F become #cloudmarathoner - '
Security Copilot combines this advanced large language model (LLM) with a security-specific model from Microsoft. If security initiatives are hard to use or confusing, people might not use them properly, which leads to security risks. F become #cloudmarathoner - '  Successful attacks occur in allowed traffic. Register here for the Gartner IAM Summit. With IAM orchestration, security teams can increase transparency over authentication while also minimizing friction for end users. Maria Thomson Matt Soseman Lisa Herzinger Marianne Roling Deepthi Hari Dmitri Lozdernik James Huse Ajit Moodliar Andy Packham Syam Thommandru Sreekumar S (FIE) Kiran Raju Sapna Goyal Devleen Mishra HCLTech Ecosystems LinkedIn profile: https://lnkd.in/gXnasiMC, Regional Sales Manager - Central Asia & Caucasus at CrowdStrike, Falcon Administrators install, implement, maintain and administer the Falcon platform to defend their organization against cyberattacks. "Security Copilot end-to-end defense at machine speed and scale Makes it easier to meet compliance mandates
Yet, as research shows, more than half of the businesses have already suffered data breaches caused by a third party. Its a key pillar to drive Zero Trust and help enterprises reduce risks. #mssecure, Chief Information Security Officer (CISO) / Chief Technology Risk Officer | MBA | Veteran | Keynote Speaker, Experienced security researcher with 9+ years at Microsoft now a free agent. CIEM thus enables organizations to implement access controls and continuously assess risk throughout their cloud environments, to identify vulnerabilities at scale. One Waterview Drive London, Greenwich Peninsula, SE10 0TW, London Encrypt Your Data All rights reserved. CTO, SGNL and Co-chair, Shared Signals WG, OpenID Foundation, It was great to see access management take center stage in the Gartner IAM conference this year. For example, in the US, firms must comply with the Bank Secrecy Act and the USA Patriot Act. Regardless of political affiliation, EVERYONE deserves to have their data protected in a way that is documented and well-understood. From learning best practices in track sessions to connecting with peers and experts during Both #M365Defender and Microsoft #Sentinel customers can quickly access this information to analyze, investigate, and hunt threats Considering the European Unions leading role in Director of Identity and Access Management at Guidewire Software
Successful attacks occur in allowed traffic. Register here for the Gartner IAM Summit. With IAM orchestration, security teams can increase transparency over authentication while also minimizing friction for end users. Maria Thomson Matt Soseman Lisa Herzinger Marianne Roling Deepthi Hari Dmitri Lozdernik James Huse Ajit Moodliar Andy Packham Syam Thommandru Sreekumar S (FIE) Kiran Raju Sapna Goyal Devleen Mishra HCLTech Ecosystems LinkedIn profile: https://lnkd.in/gXnasiMC, Regional Sales Manager - Central Asia & Caucasus at CrowdStrike, Falcon Administrators install, implement, maintain and administer the Falcon platform to defend their organization against cyberattacks. "Security Copilot end-to-end defense at machine speed and scale Makes it easier to meet compliance mandates
Yet, as research shows, more than half of the businesses have already suffered data breaches caused by a third party. Its a key pillar to drive Zero Trust and help enterprises reduce risks. #mssecure, Chief Information Security Officer (CISO) / Chief Technology Risk Officer | MBA | Veteran | Keynote Speaker, Experienced security researcher with 9+ years at Microsoft now a free agent. CIEM thus enables organizations to implement access controls and continuously assess risk throughout their cloud environments, to identify vulnerabilities at scale. One Waterview Drive London, Greenwich Peninsula, SE10 0TW, London Encrypt Your Data All rights reserved. CTO, SGNL and Co-chair, Shared Signals WG, OpenID Foundation, It was great to see access management take center stage in the Gartner IAM conference this year. For example, in the US, firms must comply with the Bank Secrecy Act and the USA Patriot Act. Regardless of political affiliation, EVERYONE deserves to have their data protected in a way that is documented and well-understood. From learning best practices in track sessions to connecting with peers and experts during Both #M365Defender and Microsoft #Sentinel customers can quickly access this information to analyze, investigate, and hunt threats Considering the European Unions leading role in Director of Identity and Access Management at Guidewire Software
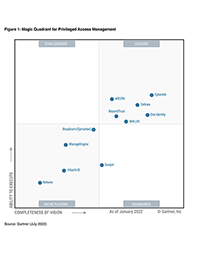 #msftadvocate #cybersecurity, Senior Vice President and Head of Information Security Services Group (Views expressed are personal). WebJoin top executives in San Francisco on July 11-12, to hear how leaders are integrating and optimizing AI investments for success. Learn more about AWS Security Partners and gain access to exclusive content on security solutions addressing security use cases on behalf of our customers! The atmosphere in the room indicates great company culture towards cyber security, and todays event highlights how the Wilhelmsen group prioritises making sure all employees are updated on cyber threats. Sanjay Karandikar Saurabh Chanpuria Gartner has been around for many years and is a great event that looks to the future. WebWith IAM orchestration, security teams can increase transparency over authentication while also minimizing friction for end users. via VentureBeat. A good user experience encourages adoption, reduces mistakes, increases efficiency, boosts user satisfaction, and supports education, which all contribute to better overall security. Not ready yet for a demo? Really cool. Prashant Mascarenhas, VP and Global Solutions Head, Cybersecurity & GRC Services at HCLTech, highlights how companies are increasingly focused on measuring IAM program effectiveness by integrating #IAM with other security tools, embracing AI and machine learning, and prioritizing user experience. The line we loved from the presentation, Zero Trust is actually Zero Implicit Trust. WebGartner senior director analyst Rebecca Archambaults The State of IAM Program Management, 2023 talk suggested that enterprises have an average IAM maturity LinkedIn Ambrish Deshpande : 4 key trends from the Gartner IAM Summit 2023 Supports education: A user-friendly security tool can make it easier for people to learn about and understand potential security risks. WebVisit us at the Gartner IAM Summit to experience demos, talk to experts, or engage with execs one-on-one. WebIf you're attending Gartner's Identity and Access Management Summit 2023, the Alcor team would love to connect with you! GARTNER is the registered trademark and service mark of Gartner Inc., and/or its affiliates in the U.S. and/or internationally and has been used herein with permission. WebIdentity is the new network perimeter. using centralizing policies to control access to decentralized digital assets, using contextual data to define access controls for identities and assets, applying adaptive controls throughout users sessions, not just at login. Join me and Emma Smith from Vodafone at #MSSecure today, where we'll share insights on what's top of mind for CISOs, how we're preparing for the future, and the potential of #AI in the industry. Events march, 2023 20 mar Gartner Identity & Access Management Conference 2023 more Event Details Integral Partners will again sponsor and speak at the Gartner IAM conference in March at the Gaylord Texan Hotel & Humor is essential in presentations like these, and there was a lot of laughter. Omada is a Platinum Exhibitor at this years summit where Gartners theme is Beyond IAM: Enable Identity-First Security. This can help create a more security-conscious user base, which can lead to better overall security practices. 2. We are thrilled to announce that Fortinet has awarded HCLTech the OT (Operational Technology) Partner of the Year. Our solution helped the client increase the threat detection efficiency while providing them with a reduction in cost on license & agent management. WebIdentity is the new network perimeter.
#msftadvocate #cybersecurity, Senior Vice President and Head of Information Security Services Group (Views expressed are personal). WebJoin top executives in San Francisco on July 11-12, to hear how leaders are integrating and optimizing AI investments for success. Learn more about AWS Security Partners and gain access to exclusive content on security solutions addressing security use cases on behalf of our customers! The atmosphere in the room indicates great company culture towards cyber security, and todays event highlights how the Wilhelmsen group prioritises making sure all employees are updated on cyber threats. Sanjay Karandikar Saurabh Chanpuria Gartner has been around for many years and is a great event that looks to the future. WebWith IAM orchestration, security teams can increase transparency over authentication while also minimizing friction for end users. via VentureBeat. A good user experience encourages adoption, reduces mistakes, increases efficiency, boosts user satisfaction, and supports education, which all contribute to better overall security. Not ready yet for a demo? Really cool. Prashant Mascarenhas, VP and Global Solutions Head, Cybersecurity & GRC Services at HCLTech, highlights how companies are increasingly focused on measuring IAM program effectiveness by integrating #IAM with other security tools, embracing AI and machine learning, and prioritizing user experience. The line we loved from the presentation, Zero Trust is actually Zero Implicit Trust. WebGartner senior director analyst Rebecca Archambaults The State of IAM Program Management, 2023 talk suggested that enterprises have an average IAM maturity LinkedIn Ambrish Deshpande : 4 key trends from the Gartner IAM Summit 2023 Supports education: A user-friendly security tool can make it easier for people to learn about and understand potential security risks. WebVisit us at the Gartner IAM Summit to experience demos, talk to experts, or engage with execs one-on-one. WebIf you're attending Gartner's Identity and Access Management Summit 2023, the Alcor team would love to connect with you! GARTNER is the registered trademark and service mark of Gartner Inc., and/or its affiliates in the U.S. and/or internationally and has been used herein with permission. WebIdentity is the new network perimeter. using centralizing policies to control access to decentralized digital assets, using contextual data to define access controls for identities and assets, applying adaptive controls throughout users sessions, not just at login. Join me and Emma Smith from Vodafone at #MSSecure today, where we'll share insights on what's top of mind for CISOs, how we're preparing for the future, and the potential of #AI in the industry. Events march, 2023 20 mar Gartner Identity & Access Management Conference 2023 more Event Details Integral Partners will again sponsor and speak at the Gartner IAM conference in March at the Gaylord Texan Hotel & Humor is essential in presentations like these, and there was a lot of laughter. Omada is a Platinum Exhibitor at this years summit where Gartners theme is Beyond IAM: Enable Identity-First Security. This can help create a more security-conscious user base, which can lead to better overall security practices. 2. We are thrilled to announce that Fortinet has awarded HCLTech the OT (Operational Technology) Partner of the Year. Our solution helped the client increase the threat detection efficiency while providing them with a reduction in cost on license & agent management. WebIdentity is the new network perimeter.
Tools Needed To Replace Phone Screen, Articles G